Encryption, authentication and data integrity in PHP
by Enrico Zimuel / @ezimuel
Senior Software Engineer
Zend a Rogue Wave Company
About me
 Developer since 1996. Senior Software Engineer at Zend a Rogue Wave Company. I did research in computer science at the Informatics Institute of Amsterdam University. Open source contributor of Apigility and Zend Framework. Author of articles and books about web programming and applied cryptography. Co-founder of PUG Torino (Italy).
Developer since 1996. Senior Software Engineer at Zend a Rogue Wave Company. I did research in computer science at the Informatics Institute of Amsterdam University. Open source contributor of Apigility and Zend Framework. Author of articles and books about web programming and applied cryptography. Co-founder of PUG Torino (Italy).
Table of contents
- Encryption in PHP
- Symmetric encryption and block ciphers
- Why encryption is not enough
- Authentication and data integrity
- Public key cryptography and digital signature
- Examples using zend-crypt of ZF2
Encryption in PHP
Mcrypt (outdated)
- Ciphers: rijndael (AES), Twofish, Blowfish, DES, 3DES, etc
- Block modes: CBC, CFB, CTR, OFB, NOFB, NCFB
- Padding: zero padding, padded with '\0'
- No Authentication!
- Suggestion: don't use it if you are not an expert!
OpenSSL
- Ciphers: RSA, AES, CAMELLIA, DES, RC2, RC4, check with openssl_get_cipher_methods()
- Block modes: CBC, CFB, CTR, ECB, XTS
- Padding: PKCS#1, No padding, SSLV23, PKCS1_OAEP
- Authenticated encryption: GCM, CCM (AEAD proposal for PHP 7.1)
Best practices for encryption
- Use AES as standard algorithm
- Use CBC or CTR mode
- Use random IVs, different for each encryption
- Generate a encryption key from user's password using a KDF function, e.g. PBKDF2
- ALWAYS authenticate the encrypted data, e.g. HMAC-SHA256
- Secure random in PHP 5: openssl_random_pseudo_bytes() (bug #70014), mcrypt_create_iv(), /dev/urandom
- Secure random in PHP 7: random_int() or random_bytes()
Why we need authentication?
- Encryption only provides confidentiality
- An attacker can easily alter the encrypted message
- Padding Oracle Attacks can be applied to retrieve the plaintext without the key!
Padding Oracle Attack
- Side channel attack which is performed on the padding of a cryptographic message
- Discovered in 2001 by Serge Vaudenay
- Works on ECB, CBC, OAEP modes for all the block ciphers
- In 2010 the attack was applied to several web application frameworks, including JavaServer Faces, Ruby on Rails and ASP.NET.
- Can be prevented using authentication (for instance, HMAC)
Attack the CBC with PKCS#7
- The Oracle is the encryption box to attack
- We send 2 blocks of ciphertext, C'1 || C2, where C'1 is random and C2 is a real ciphertext block
- The Oracle returns 1 if the padding is valid, 0 if not
- We try C'1[i] = 0..255, until Oracle is valid, for i = 15..0
- If C'1[i] = x produces a valid padding, we can retrieve the i-byte of the plaintext
Attack the intermediate state
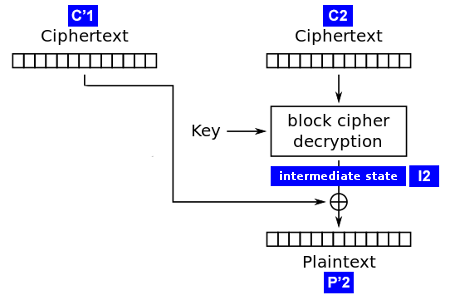
P'2 = I2 ⊕ C'1 ⇒ I2 = P'2 ⊕ C'1
We know C'1[i] = x ⇒ we know I2[i]
I2 is the same as in the real ciphertext ⇒ P2[i] = C1[i] ⊕ I2[i]
AES encryption + HMAC-SHA256
function AES_encrypt($text, $key) {
$ivsize = openssl_cipher_iv_length('aes-256-cbc');
$iv = openssl_random_pseudo_bytes($ivsize);
// Encryption key generated by PBKDF2 (since PHP 5.5)
$keys = hash_pbkdf2('sha256', $key, $iv, 10000, 64, true);
$encKey = substr($keys, 0, 32); // 256 bit encryption key
$hmacKey = substr($keys, 32); // 256 bit hmac key
$ciphertext = openssl_encrypt(
$text,
'aes-256-cbc',
$encKey,
OPENSSL_RAW_DATA,
$iv
);
$hmac = hash_hmac('sha256', $iv . $ciphertext, $hmacKey);
return $hmac . $iv . $ciphertext;
}AES decryption + HMAC-SHA256
function AES_decrypt($text, $key) {
$hmac = substr($text, 0, 64);
$ivsize = openssl_cipher_iv_length('aes-256-cbc');
$iv = substr($text, 64, $ivsize);
$ciphertext = substr($text, $ivsize + 64);
// Generate the encryption and hmac keys
$keys = hash_pbkdf2('sha256', $key, $iv, 10000, 64, true);
$encKey = substr($keys, 0, 32); // 256 bit encryption key
$hmacNew = hash_hmac('sha256', $iv . $ciphertext, substr($keys, 32));
if (!compareStrings($hmac, $hmacNew)) { // to prevent timing attacks
return false;
}
return openssl_decrypt(
$ciphertext,
'aes-256-cbc',
$encKey,
OPENSSL_RAW_DATA,
$iv
);
}Timing attacks?
A timing attack is a side channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms
From Wikipedia
Use hash_equals() to prevent timing attacks (PHP 5.6+)
Public key encryption
&
Digital signature
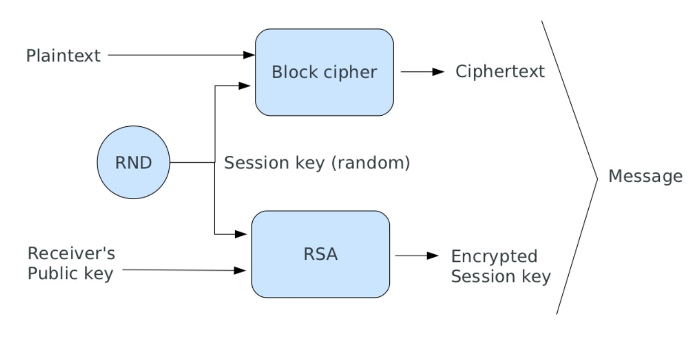
Hybrid cryptosystem
Public key algorithms are too slow to encrypt a full text message
We need a different approach (Hybrid cryptosystem):
- generate a random key;
- encrypt the key using a public key algorithm;
- encrypt the message with a symmetric cipher;
- send the ciphertext and the encrypted key;
Generate public and private keys
// Generate public and private keys
$keys = openssl_pkey_new(array(
"private_key_bits" => 4096,
"private_key_type" => OPENSSL_KEYTYPE_RSA,
));
// Store the private key in a file
$passphrase = 'test';
openssl_pkey_export_to_file($keys, 'private.key', $passphrase);
// Store the public key in a file
$details = openssl_pkey_get_details($keys);
$publicKey = $details['key'];
file_put_contents('public.key', $publicKey);
Hybrid encryption
$message = 'This is the secret message';
$passphrase = 'test'; // to read the private key
// Encryption
$key = openssl_random_pseudo_bytes(32);
openssl_public_encrypt($key, $encryptedKey, $publicKey);
$ciphertext = AES_encrypt($message, $key);
file_put_contents('encrypted.msg', $encryptedKey . $ciphertext);
// Decryption
$ciphertext = file_get_contents('encrypted.msg');
$encKey = substr($ciphertext, 0, 512);
$ciphertext = substr($ciphertext, 512);
$privateKey = openssl_pkey_get_private('file:///path/to/private.key',
$passphrase);
openssl_private_decrypt($encKey, $key, $privateKey);
$result = AES_decrypt($ciphertext, $key); // equal to $message
Digital signature
- How to provide authentication and non-repudiation?
- A digital signature is a mathematical scheme for demonstrating the authenticity of a digital message or document
- Commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery or tampering

Signature with OpenSSL
// Compute the signature
$passphrase = 'test';
$privateKey = openssl_pkey_get_private('file:///path/to/private.key',
$passphrase);
$data = file_get_contents('/path/to/file_to_sign');
openssl_sign($data, $signature, $privateKey, "sha256");
printf("Signature : %s\n", base64_encode($signature));
// Verify the signature
$publicKey = openssl_pkey_get_public('file:///path/to/public.key');
$result = openssl_verify($data, $signature, $publicKey, "sha256");
echo $result === 1 ? 'Signature verified' : 'Signature not valid';
Cryptography with zend-crypt
zend-crypt is the cryptographic component of ZF2
- Encrypt-then-authenticate (Zend\Crypt\BlockCipher)
- File encryption/decryption
- Public key and digital signature (Zend\Crypt\PublicKey)
- Key derivation function (e.g. PBKDF2 since PHP 5.3)
- Secure password hashing (e.g. bcrypt since PHP 5.3)
- HMAC and Hash functions
AES + HMAC-SHA256 in ZF2
use Zend\Crypt\BlockCipher;
$blockCipher = BlockCipher::factory('mcrypt', array('algo' => 'aes'));
$blockCipher->setKey('encryption key');
$ciphertext = $blockCipher->encrypt('this is a secret message');
Public key crypto in ZF2
use Zend\Crypt\PublicKey\RsaOptions;
use Zend\Crypt\PublicKey\Rsa;
// Generate public and private key
$rsaOptions = new RsaOptions(array( 'pass_phrase' => 'test' ));
$rsaOptions->generateKeys(array( 'private_key_bits' => 2048 ));
file_put_contents('private_key.pem', $rsaOptions->getPrivateKey());
file_put_contents('public_key.pub', $rsaOptions->getPublicKey());
// Sign and verify
$rsa = Rsa::factory(array(
'private_key' => 'path/to/private_key',
'pass_phrase' => 'passphrase of the private key'
));
$file = file_get_contents('path/file/to/sign');
$sign = $rsa->sign($file, $rsa->getOptions()->getPrivateKey());
$verify = $rsa->verify($file, $sign, $rsa->getOptions()->getPublicKey());
References: articles and books
- Serge Vaudenay, Security Flaws Induced by CBC Padding Applications to SSL, IPSEC, WTLS..., EUROCRYPT 2002
- J. Rizzo, T. Duong, Practical Padding Oracle Attacks, USENIX WOOT 2010
- M. Bellare, C. Namprempre, Authenticated Encryption: Relations among notions and analysis of the generic composition paradigm, ASIACRYPT 2000
- D. Brumley, D. Boneh, Remote Timing Attacks are Pratical, USENIX Security Symposium, August 2003
- N. Ferguson, B. Schneier, T. Kohno, Cryptography Engineering, John Wiley & Sons, 2010
- Joshua Davies, Implementing SSL / TLS Using Cryptography and PKI, John Wiley & Sons, 2011
- A.J. Menezes, P.C. van Oorschot, S.A. Vanstone, Handbook of Applied Cryptography, CRC Press, 2001
- Ross J. Anderson, Security Engineering, John Wiley & Sons, 2008
References: blog and websites
- Rob Heaton, The Padding Oracle Attack - why crypto is terrifying, 29 Jul 2013
- Dennis Fisher, Padding Oracle’ Crypto Attack Affects Millions of ASP.NET Apps, 13 Set 2010
- J. Rizzo, T. Duong, Practical Padding Oracle Attacks (slides), Black Hat Europe, 2010
- Brian Holyfield, Automated Padding Oracle Attacks with PadBuster, 14 Set 2010
- Moxie Marlinspike, The Cryptographic Doom Principle, 13 Dec 2011
- Matthew Green, How to choose an Authenticated Encryption mode, Hopkins University, 19 May 2012
- Dan Boneh, Cryptography course Stanford University, Coursera
- Thomas & Erin Ptacek, Applied Cryptography Engineering, 22 July 2013
- Thomas Hühn, Myths about /dev/urandom, 20 March 2014
- Timo, Secure random numbers for PHP developers, 8 Nov 2013
- Timo, PHP data encryption primer, 16 June 2014
- Pádraic Brady, Nanosecond Scale Remote Timing Attacks On PHP Applications: Time To Take Them Seriously?, 20 Oct 2010
Thanks!
Rate this talk at joind.in/talk/8ea10
Contact me: enrico [at] zend.com
Follow me: @ezimuel

This work is licensed under a
Creative Commons Attribution-ShareAlike 3.0 Unported License.
I used reveal.js to make this presentation.

